Media coverage: VICE, ITWorld, Metro News Canada, PC World and Toronto Star.
It is well known that advertisers track people’s web browsing habits across the Internet, but what’s less well known is that this tracking is largely done in an insecure manner. As demand for secure technology grows, most websites will not be able to protect their readers unless they stop using insecure ad trackers. To expose this problem and give people tools to help encourage websites to adopt stronger security practices, we have developed a Chrome browser extension called TrackerSSL. The extension is a collaboration between Open Effect, the non-profit I direct, and the Citizen Lab.
TrackerSSL addresses the widespread use of unencrypted data transmissions on the web that leave people vulnerable to mass surveillance from state agencies and network operators. While encrypted web traffic has traditionally been associated with services such as online banking, the Snowden revelations and other stories have driven a growing movement to encrypt the entire web. TrackerSSL seeks to inform people on the web about some of the obstacles websites face if they intend to protect their readers’ privacy and security. The extension also empowers people to join a conversation about encrypting the web with HTTPS.
For each web page visited, TrackerSSL displays the percentage of ad trackers that support basic HTTPS security. A more detailed report specifies the names of secure and insecure tracking companies, and displays a list of trackers that are using unique identifiers to track a user’s behaviour, securely or otherwise.
For example, looking at a Washington Post article about how news sites could protect your privacy but probably won’t, TrackerSSL shows that 55% of the page’s 36 trackers could be securely transmitting user browsing data, while 9 trackers use unique identifiers to track the user across web pages. If the Post were committed to its website becoming secure, it might encourage the remaining 45% of its trackers to adopt HTTPS, or replace them with trackers that do.
TrackerSSL’s accompanying Twitter button invites the user to start a conversation about a website’s privacy and security; clicking the button opens up a window with a prewritten tweet that reads “Hey @washingtonpost, most of your site’s ad trackers support HTTPS. Why don’t you secure your readership and do the same? #trackerSSL”.
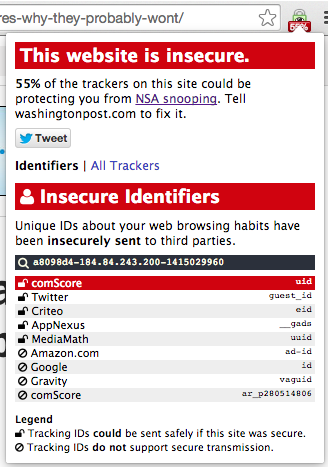
TrackerSSL report for a web page.
The following is a high level overview of TrackerSSL’s user experience.
Encrypt the web
Unencrypted transmissions enable anyone with a position of power on a network (such as Internet Service Providers or state surveillance agencies) to snoop on the content of one’s web browsing activities. For content-driven websites such as online newspapers, such snooping can take the form of what’s known as “pattern of life analysis”. Analysts may compile the web browsing history of a target and build the profile of a target by inferring from the target’s lifestyle, demographics, political views, and more.
While ad trackers are deployed primarily to serve personalized advertisements, the NSA is known to piggyback on ad trackers’ user-identifying cookies to help them assemble detailed profiles about their targets.
Encrypted transmissions using the HTTPS standard prevent network snoops from knowing the content of communications between party A and party B. They also ensure that the content received by an end user indeed originated from the intended party, combatting network injection attacks.
Unfortunately, implementing HTTPS on a web server is by no means easy. Certain web hosts do not support HTTPS, buying the right kind of certificate can be tricky and expensive, and ensuring that all your site’s links default to HTTPS instead of HTTP can be a pain. To make matters worse, the security is only effective if all the third parties that provide advertisements, images, and other content on a website also use HTTPS. If just one out of a dozen third-parties on a website do not use HTTPS, then a gaping security hole is left open.
Content-driven websites rely heavily on ad trackers and other third parties to gather revenue and operate their services. Unfortunately, many of these trackers do not support HTTPS, and therefore are a major factor in blocking the widespread adoption of the security protocol amongst websites. TrackerSSL exposes the true scope of this barrier for each web page visited. If a majority of trackers on a given web site do indeed support HTTPS, then the site itself has less of an excuse for not securing its readership.
How TrackerSSL Works
TrackerSSL reveals the transit security capabilities of each web page and its third party ad trackers. The Google Chrome extension displays whether a website uses insecure third-party trackers that could stop a news organization from immediately implementing HTTPS or, alternately, where a website has made the choice to use non-secure over secure third-party trackers.
TrackerSSL works by running a series of tests on each and every web request issued by your web browser. It identifies requests sent to third parties (sites besides the domain of the page you are currently on), and identifies the third party using the Disconnect list of known trackers. It then uses the Electronic Frontier Foundation’s HTTPS Everywhere project’s rulesets (among other methods) to check whether or not those third parties support HTTPS. TrackerSSL also checks these third party requests for the presence of persistent identifier cookies, and categorizes them by whether or not the request could have been made more securely.
The result of these tests is a compact report for each page you load. The report outlines the percentage of third parties that could support HTTPS if the host website itself did.
A Twitter button provides users with the ability to post pre-written tweets, whose text varies from congratulating a page for being served through HTTPS, asserting the site should adopt HTTPS if it has a high percentage score, and arguing a site should adopt more secure trackers if it has a low percentage score.
The web we have and the web we want
TrackerSSL aims to increase awareness and encourage a conversation about stronger privacy and security practices. In addition, TrackerSSL lets readers communicate this to website operators via Twitter.
The web we have is at the moment largely insecure, but tools like TrackerSSL are meant to encourage better security practices so that we can all enjoy the safe, private web we want.
Resources
TrackerSSL in the Google Chrome Store.
Vote for TrackerSSL in Ghostery’s “Hack The Trackers” Challenge (registration required).
GitHub Repository for the project.
Acknowledgements
TrackerSSL hackathon team: Guilherme Alberto Almeida de Almeida, Garrett Jeffrey

 Request access to your personal data with our simple tool
Request access to your personal data with our simple tool



